POSTED BY Charles E. Root Jr. MS. AT 9:59 A.M. Nov 14, 2016
When a corporation purchases another company, the contract for acquisition generally includes something called a “material-adverse-change clause,” or MACC. This clause allows buyers to withdraw or alter a deal if the value of a transaction has been hurt by a significant development, such as a situation in which the company being purchased incurs the largest data breach of customer information in all of recorded history.
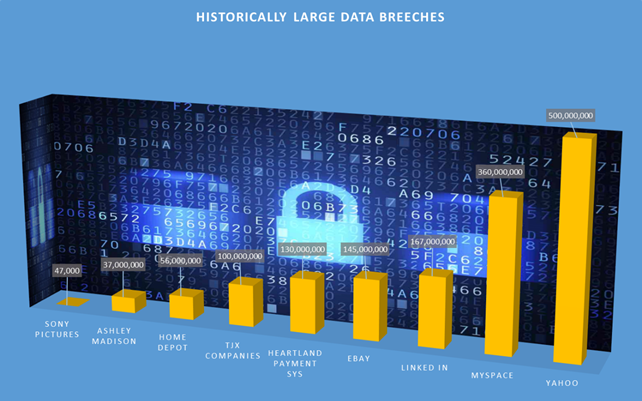
Verizon is now in just such a situation. They were recently informed by Yahoo, a company they inked a $4.8 billion purchase of back in July, that in 2014, Yahoo’s servers were hacked and over 500 million Yahoo user accounts loaded with personal data were stolen. Now, various reports in the news are suggesting Verizon is going to ask for a $1 billion reduction in the price of the deal.
Let’s consider customer data for a moment. When a business collects customer data, this data becomes part of the business’s overall intellectual property portfolio. This data is an intangible asset and has significant value. (For another view on customer data and its value see “Capital Market Pricing of Opaque Intangible Assets”.) While there are numerous legal obligations in place to ensure the privacy of customer data, it is also in a business’s own best interest to handle this data as it would any other intellectual property, i.e., as a very valuable asset. Such diligence allows the business to avoid the sort of headaches that Verizon is currently dealing with.
How do we approach keeping customer data, and through that, our own IP safe? Well first, don’t make billion dollar purchases without first conducting very thorough due diligence, including a complete security audit of the company’s databases. But most of us won’t be buying a Yahoo or LinkedIn, so below are some items to consider.
The Basics:
Use A Hardware Firewall: If you’re only using a software firewall, hackers have already opened your door, and you’re battling them on your own turf. Keep them a complete step away from your network with a good appliance firewall.
Stop Hosting Your Own E-mail: It may seem counterintuitive, but if you run an Exchange Server, unless you’ve got an entire IT team dedicated to maintaining just that e-mail server and nothing else, then you are creating an easily exploitable hole in your network. Move your e-mail to the cloud with Office 365 or Corporate Gmail. They have significantly more robust security then you could ever place around your own Exchange Server.
Keep All Your PCs Up-To-Date: Having up to date OSs, web browsers, applications and security software, defends against known viruses, malware, and other online threats.
Automate Software Updates: While the risk of getting an update that “bricks” your computer isn’t non-zero, turning on automatic software updates will keep your software updated to the latest version and protected from known risk. Better yet, use a patch management program like Shavlik.
Scan External Devices: No USB thumb drive, smartphone, or even printer should be allowed on your network without being scanned by security software first. Best practice is to lock out USB ports on end PCs.
Advanced IT:
Encryption: Keep all your data encrypted so that if it is stolen, it’s unreadable by thieves. Windows Server 2012, Windows 10, and all Linux distributions offer full disk 256-bit encryption.
Air Gap Customer Data: Only keep customer data on a machine that is not physically connected to the internet. This requires regular nightly imports of data from machines collecting data via specialized process, but once the data is imported it’s erased from the collecting PC.
Blockchain Your Databases: A blockchain is a distributed database, usually cloud-based, but can be done using private servers (altchains). The database uses a continuously growing list of records called blocks. Each block contains a timestamp and a link to a previous block, forming a virtual chain secure from tampering. The cryptocurrency BitCoin uses this technology for security.
Run Constant DB Auditing: Almost all database packages such as SQL have an audit function. This should be turned on. The audit process should be run on an independent computer; not on the system being audited. The audit trail should capture as much data as possible so the “heavy” option should be chosen when setting up the audit logs.
Now, no system is 100% secure, and if you’re facing a state-sponsored attack where it’s a government with essentially unlimited resources, odds are they will find a way in. The trick is minimizing the impact. If all the data they can get is encrypted and spread out over multiple servers, it is only collated and decrypted when the proper keys are given. If they do steal your IP, and thus your customer private data, the best they’ll ever get is:
—–BEGIN ENCRYPT MESSAGE—–
Encryption-Info: AES-128,CBC,PKCS5 Padding
Key-Info: MD5,PBKDF2 HmacSHA1
3+62RCd7iGKFMo wH68NRLKC0iaKv+E Zd+Udn6u4XHG6G5tWk BUetIN5L2X6MmjwJ
—–END ENCRYPT MESSAGE—–
(The encrypted message above is the word “Garbage”)
If Yahoo had implemented some of these advanced measures, Verizon might not today be getting cold feet on their multi-billion dollar deal.

